Unfortunately, there is an another incident of data breach. This time Twilio which has disclosed that attackers tricked an employee into sharing their credentials. Meaning allowing them to access information for a “limited number” of customers.
A ‘sophisticated’ SMS phishing attack on Twilio employees allowed hackers to access some customer data. The company said it has been notifying affected customers individually. “If you are not contacted by Twilio, then it means we have no evidence that your account was impacted by this attack,” the company said.
The company did not disclose how many customers were affected or what types of data may have been accessed. In an effort to stave off additional breaches, Twilio said it’s working with those companies. Among the actions they’re taking is asking mobile carriers to block “malicious messages” in the first place and asking hosts and registrars to shut down the URLs used to trick employees.
Official Twilio Statement
On August 4, 2022, Twilio became aware of unauthorized access to information related to a limited number of Twilio customer accounts through a sophisticated social engineering attack designed to steal employee credentials. This broad based attack against our employee base succeeded in fooling some employees into providing their credentials.
The attackers then used the stolen credentials to gain access to some of our internal systems, where they were able to access certain customer data. We continue to notify and are working directly with customers who were affected by this incident. We are still early in our investigation, which is ongoing.
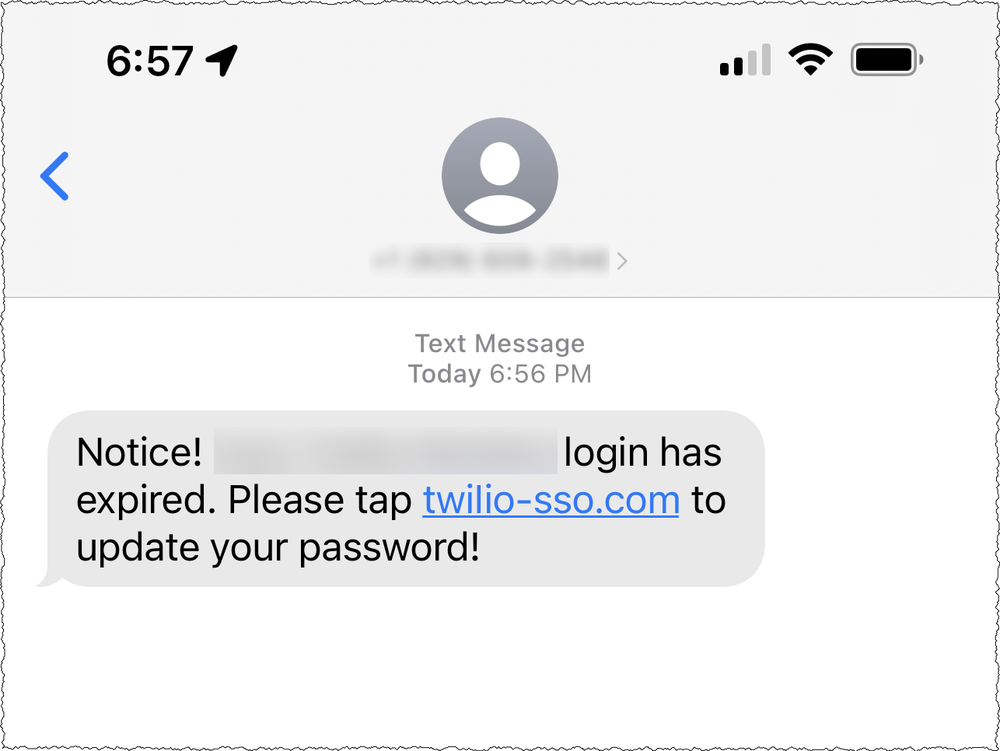
More specifically, current and former employees recently reported receiving text messages purporting to be from our IT department. Typical text bodies suggested that the employee’s passwords had expired, or that their schedule had changed, and that they needed to log in to a URL the attacker controls. The URLs used words including “Twilio,” “Okta,” and “SSO” to try and trick users to click on a link taking them to a landing page that impersonated Twilio’s sign-in page.
The text messages originated from U.S. carrier networks. We worked with the U.S. carriers to shut down the actors and worked with the hosting providers serving the malicious URLs to shut those accounts down. Additionally, the threat actors seemed to have sophisticated abilities to match employee names from sources with their phone numbers.
Once the incident was confirmed, Twilio’s security teams revoked access to the compromised employees to halt the attack. A leading forensics firm was engaged to aid Twilio’s ongoing investigation.
However, the company has yet to discover who conducted the successful attack. The company further said: They will perform an extensive post-mortem on the incident and begin “instituting betterments to address the root causes” of the compromise.
University of Email doesn't confirm this news as this has been brought here based on our research.

